How to describe your experience to get any cyber security jobs you want. Seeking a challenging position as a cyber security specialist with abc company that promotes learning and growth and needs a highly motivated and skilled employee.

Recruitment Consultant Cv Example Land A Top Recruitment Job
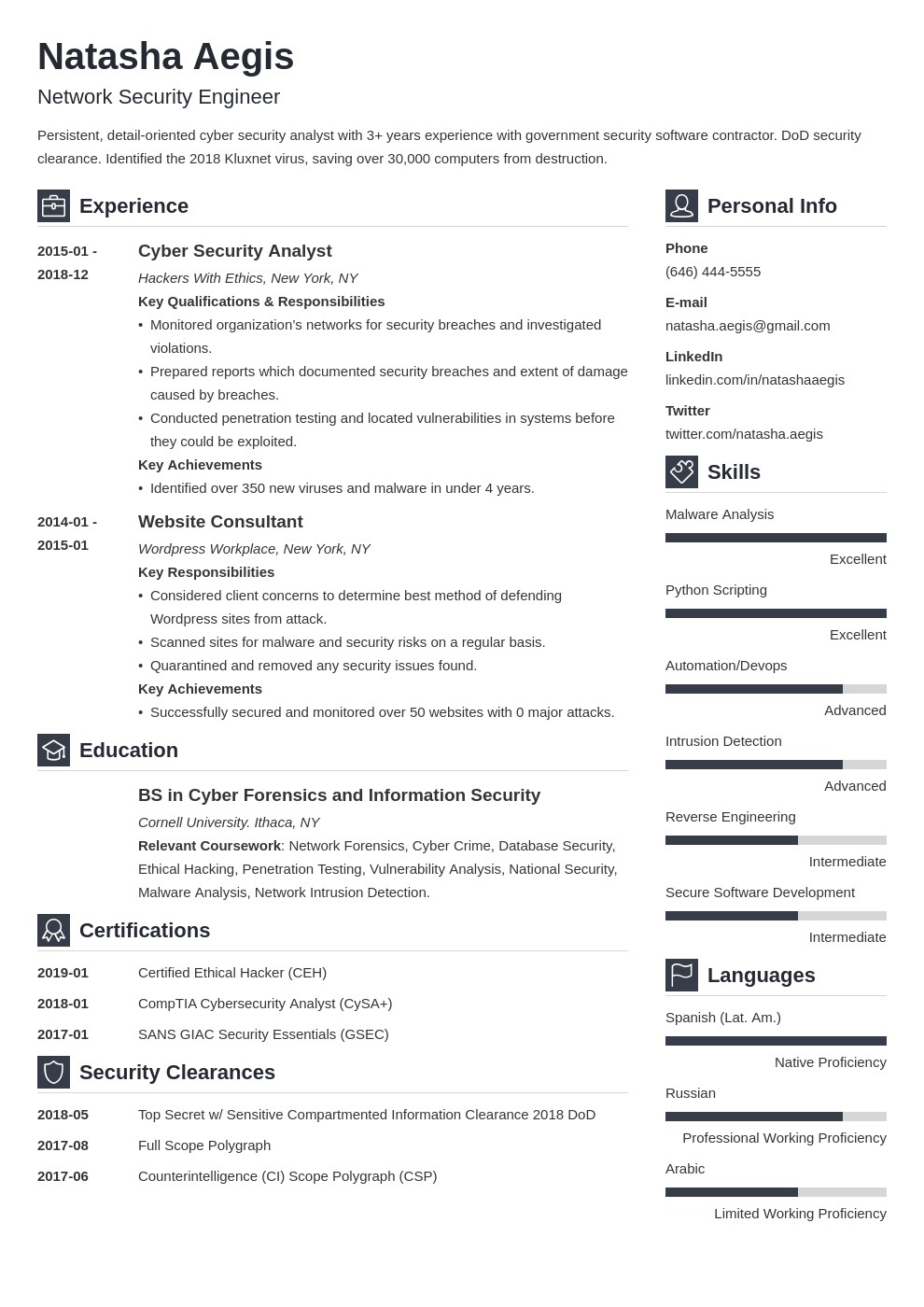
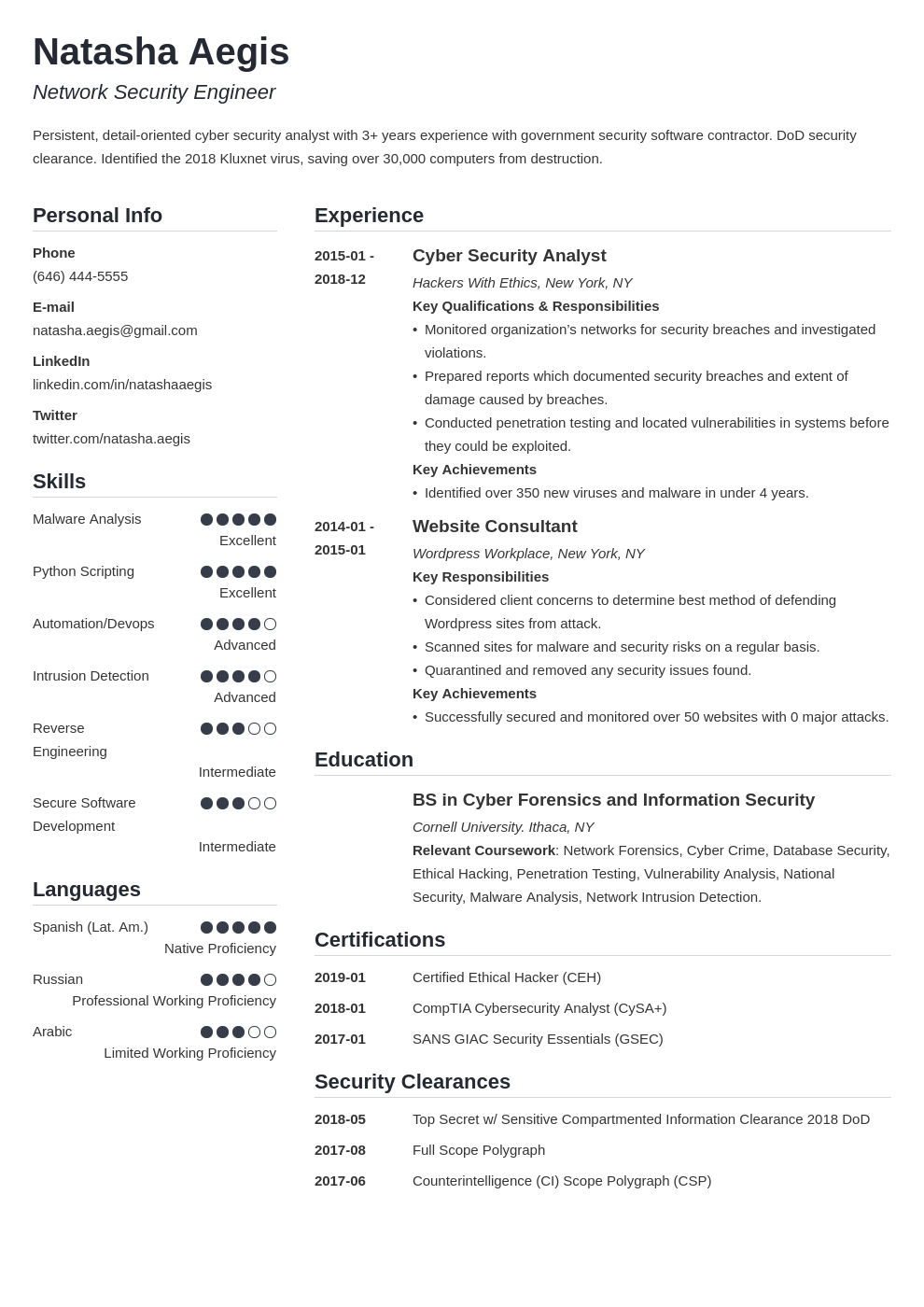
Network security consultant cv. Network scanning and mitigation of servers and workstations. Information security resume examples better than 9 out of 10 other resumes. Jul 29 2020 location. Patch application in accordance with iavm disa fso standards. Led the information vulnerability management ivm process at adnet to ensure compliance and increase the networks security posture. Cyber security specialist with experience in cloud computing and private corporate security systems.
Tips on how to put skills and achievements on an it security resume. Download the information security analyst cover letter template compatible with google docs and word online or see below for more examples. To get you started here are some resume objective examples for your customization and use. Analyzing security risks determining the most effective way to protect computers interviewing staff on security issues adhering to security standards and testing security solutions. Information security analyst cover letter example. A successful associate consulting engineer ace will immerse in a close knit group of techies to collaborate and master with.
How to write a cyber security resume that gets more interviews. San diego ca united states cdw is building teams that are growing service offerings to our customers. Network security consultants reduce the vulnerability of complex network systems and prevent unauthorized access. Sample cyber security specialist resume objectives. This is an example of a cover letter for an information security analyst job. Their job involves the following work activities.
This cyber security resume guide will show you. Past work experience includes not only high security environments but also with low security network systems open to the. Training includes intrusion management and threat detection for api systems and department of defense intensive training.